In 2025, data breaches have become an everyday occurrence. Every year, billions of emails, passwords, phone numbers, and banking details are exposed as a result of cyberattacks targeting companies, websites, and apps. Yet 80% of victims are unaware that their data is circulating on the dark web, according to a recent study by ANSSI.
The consequences? Identity theft, account hacking, highly targeted phishing, and loss of privacy. Fortunately, there are free and accessible tools that allow you to check in just a few clicks whether your information has been compromised. Here is a practical guide to regaining control of your digital security.
1. Three essential tools for tracking down leaks
– Have I Been Pwned: the global benchmark
Created by cybersecurity expert Troy Hunt, Have I Been Pwned is the world’s most comprehensive database, with over 17 billion exposed accounts listed.
But how do you use it?
– Enter your email address.
– The site displays a list of leaks where your data appears, with details about the information exposed (passwords, addresses, etc.).
– Follow-up option: Receive real-time alerts in the event of a new leak after registering your email address.
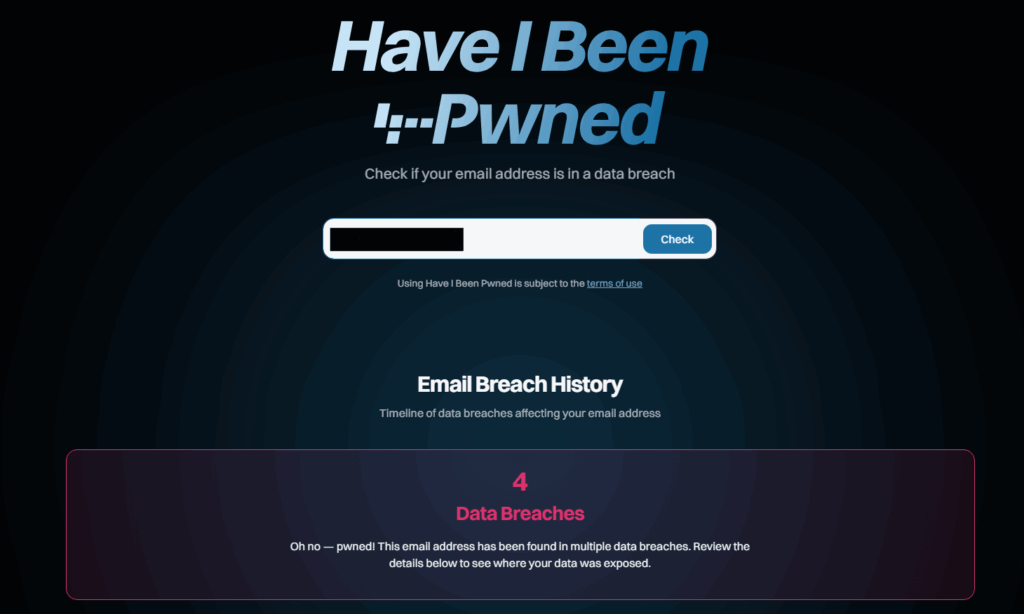

Why is it effective? Have I Been Pwned is continuously updated and collaborates with companies and governments to identify new cyberattacks.
– Firefox Monitor: simplicity in the service of security
Developed by Mozilla, Mozilla Monitor is based on the Have I Been Pwned database, but with a more intuitive interface and personalized advice
– Its strengths:
– Instant scan of your email.
– Alerts integrated directly into your Firefox browser.
– Clear reports explaining what data has been leaked and how to respond.

Ideal for: Users looking for a simple, educational solution without technical jargon.
– HPI Identity Leak Checker: the european swiss army knife
Offered by the Hasso Plattner Institute (Germany), HPI Identity Leak Checker stands out for its detailed, European approach, which complies with the GDPR.
– But how do you use it?
– Enter your email address.
– A comprehensive report will be sent to you by email, including:
– A comprehensive report will be sent to you by email, including:
– The services affected (LinkedIn, Facebook, etc.).
– The type of data exposed (passwords, phone numbers, IP addresses).
– A risk level (low, medium, high).
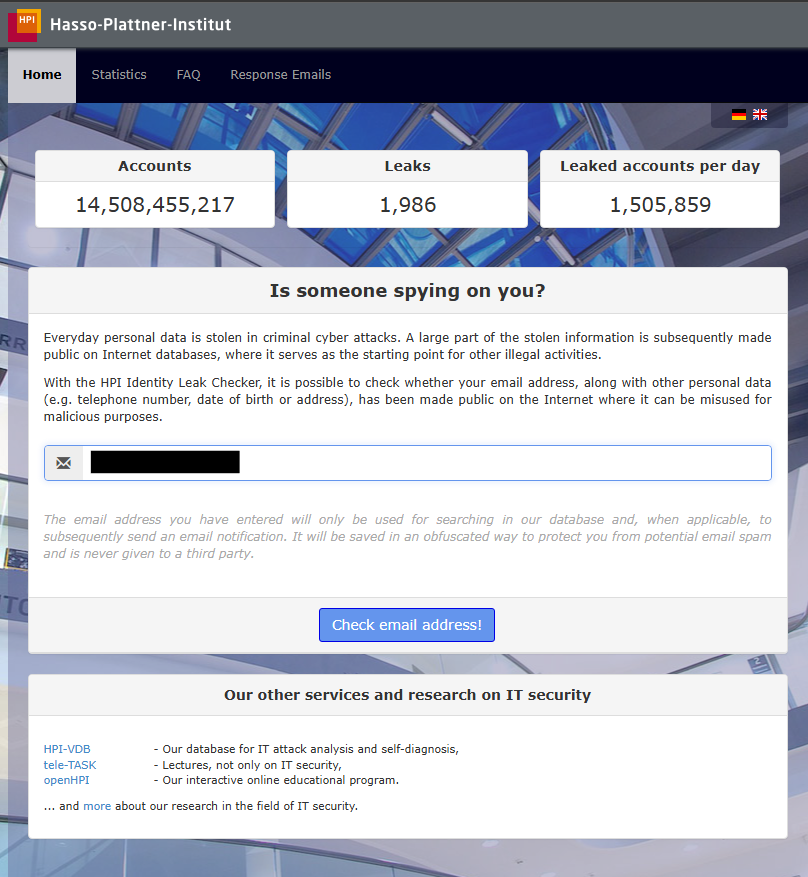
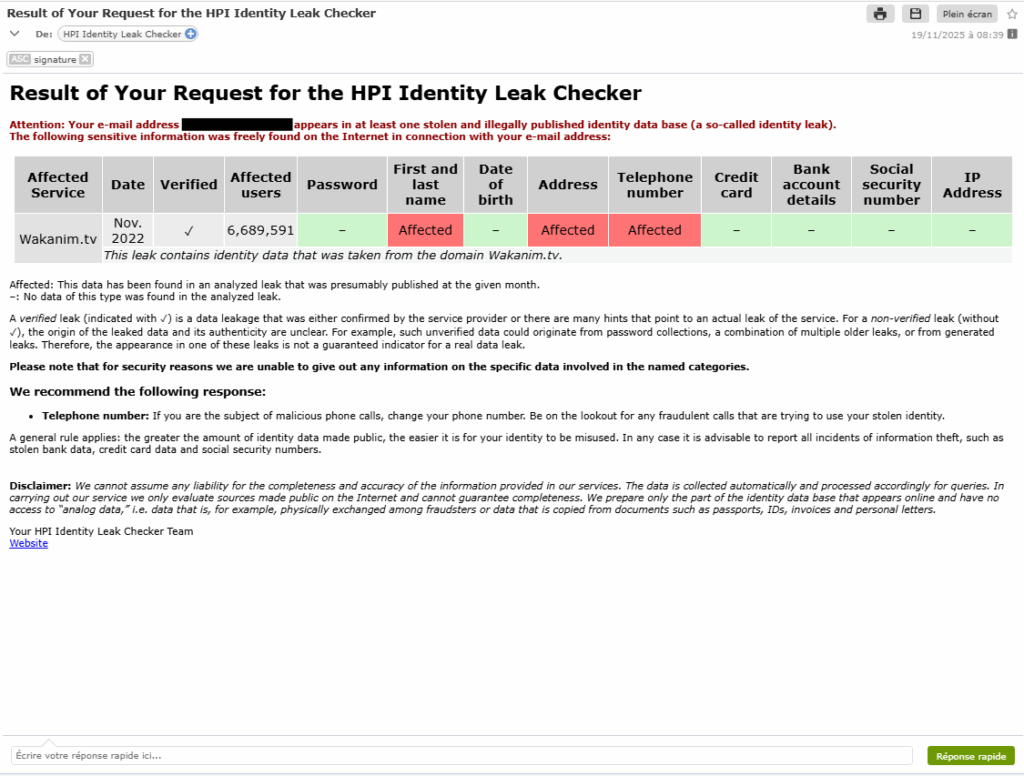
Why use it? Unlike other tools, HPI provides precise explanations about the severity of the leak and the measures to be taken.
– What to do if your data has been leaked? A 5-step action plan
– Change your passwords immediately.
– Use unique and complex passwords (example: C0r@l-Rec!f-2025#).
– Avoid dictionary words or personal information.
– Enable two-factor authentication (2FA)
– Choose apps like Google Authenticator over SMS (which is vulnerable to hacking).
– Delete unused accounts
– Fewer accounts = fewer risks. Use JustDeleteMe to easily deactivate them.
– Use a password manager
– Bitwarden, 1Password, or KeePass generate and store secure passwords.
– Monitor your accounts regularly
– Check your data every 3 to 6 months and enable automatic alerts.
(sec.hpi.de)
(haveibeenpwned.com)
(monitor.mozilla.org)
(justdeleteme.xyz)
(bitwarden.com)
(1password.com)
(keepass.info)